ThreatModeler Software Pricing, Features & Reviews
What is ThreatModeler?
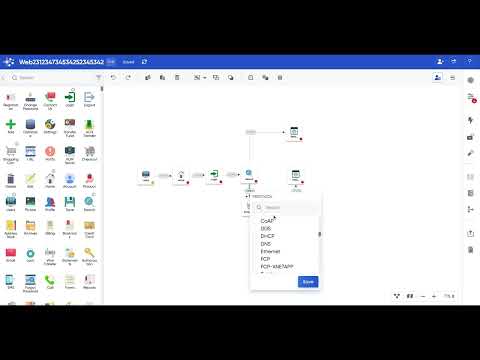
ThreatModeler is a leading automated threat modelling platform designed to empower developers, architects, and security professionals to build secure software from the ground up. It provides an intuitive interface, pre-built threat libraries, and seamless integration with existing development workflows. The platform helps identify and mitigate potential security vulnerabilities in software early in the development cycle.
It uses the STRIDE methodology to analyze system architecture and generate potential threats. It also includes real-time collaboration, detailed reporting, and compliance support for industry standards like OWASP and NIST. The platform is scalable, modular, and adaptable, making it suitable for organizations of all sizes and complexities.
Why Choose ThreatModeler Software?
- Automated Threat Generation: Analyzes system architecture and generates potential threats using industry best practices and the STRIDE methodology.
- Visual and Collaborative Approach: Creates clear diagrams to visualize systems, threats, and mitigations, enabling real-time user collaboration.
- Seamless Integration with Development Tools: Integrates with Git repositories, CI/CD pipelines, and issue trackers to embed security into existing workflows.
- Compliance Support: Aligns with standards and regulations like OWASP, NIST, PCI DSS, and GDPR to help meet security requirements.
- Detailed Reporting: Generates comprehensive reports summarizing threat models, identified threats, chosen mitigations, and decision rationales for stakeholders and auditors.
- Empowering Non-Security Experts: Provides an intuitive interface and pre-built threat libraries for developers, architects, and security professionals of all skill levels.
- Continuous Threat Modeling: Automatically updates risk exposure by monitoring real-time changes to the threat landscape and IT environment.
Benefits of ThreatModeler Platform
- Scalability: Handles large, complex environments, ideal for enterprises with extensive IT infrastructures.
- Automation and Efficiency: Automates threat modelling, reducing the time and effort needed to identify security issues and allowing focus on mitigation and resolution.
- Enhanced Security Posture: Continuously monitors and updates the threat model, helping maintain a proactive security stance and reducing unnoticed vulnerabilities.
- Actionable Insights: Provides actionable insights and recommendations, enabling effective threat prioritization and resource allocation.
- User-Friendly Interface: Features an intuitive design, ensuring easy navigation and use, minimizing the learning curve and maximizing productivity.
- Real-Time Collaboration: Supports real-time collaboration, enhancing communication and coordination among team members for effective threat modelling and mitigation.
- Adaptability: Adapts to various development methodologies, including Agile and DevOps, integrating seamlessly into the software development lifecycle.
- Customizability: Allows customization of threat libraries and templates to meet specific organizational needs and unique requirements.
- Robust Support and Community: Offers strong customer support and a community of users and experts for assistance and best practice sharing.
- Cost-Effective Security: Prevents security breaches and reduces the need for costly post-incident responses, providing a cost-effective cybersecurity solution.
Pricing of ThreatModeler
ThreatModeler price details are available on request at techjockey.com.
The pricing model is based on different parameters, including extra features, deployment type, and the total number of users. For further queries related to the product, you can contact our product team and learn more about the pricing and offers.









20,000+ Software Listed
Best Price Guaranteed
Free Expert Consultation
2M+ Happy Customers