How to Accelerate and Secure Cloud-Native Applications with NGINX

Cloud-native is an approach designed to exploit the benefits of cloud-native app delivery. Adapting cloud-native technology means a business would be able to meet both the consumer and market demand faster.
As per an SPI management survey commissioned by NGINX, nearly 35 percent of all business applications will be on the cloud by 2022. Cloud-native app delivery promises an outstanding digital experience for customers.
However, it poses higher risks to data security. Let’s learn about cloud-native applications and the risks associated with them.
What are Cloud Native Applications?
A cloud-native app is designed to deliver a consistent development and management experience across public, private, and hybrid clouds. The cloud native approach increases the scalability and availability of business applications.
The entire application lifecycle is automated on the cloud to ensure better provisioning of resources. Additionally, cloud-native applications also enjoy the benefits like higher uptime, better digital service for customers, and quick disaster recovery.
The cutting-edge technology works in both private and public cloud, and aside from decreased vendor lock-ins, the pay-per-use model makes it easy to shift to a multi-cloud architecture.
However, you need to take robust measures to ensure the security of cloud native applications in the hybrid cloud setup.
Suggested Read: NGINX Vs NGINX Plus: Why Upgrade from Open Source to Commercial Version
What are the Risks Associated with Cloud Native App Delivery?
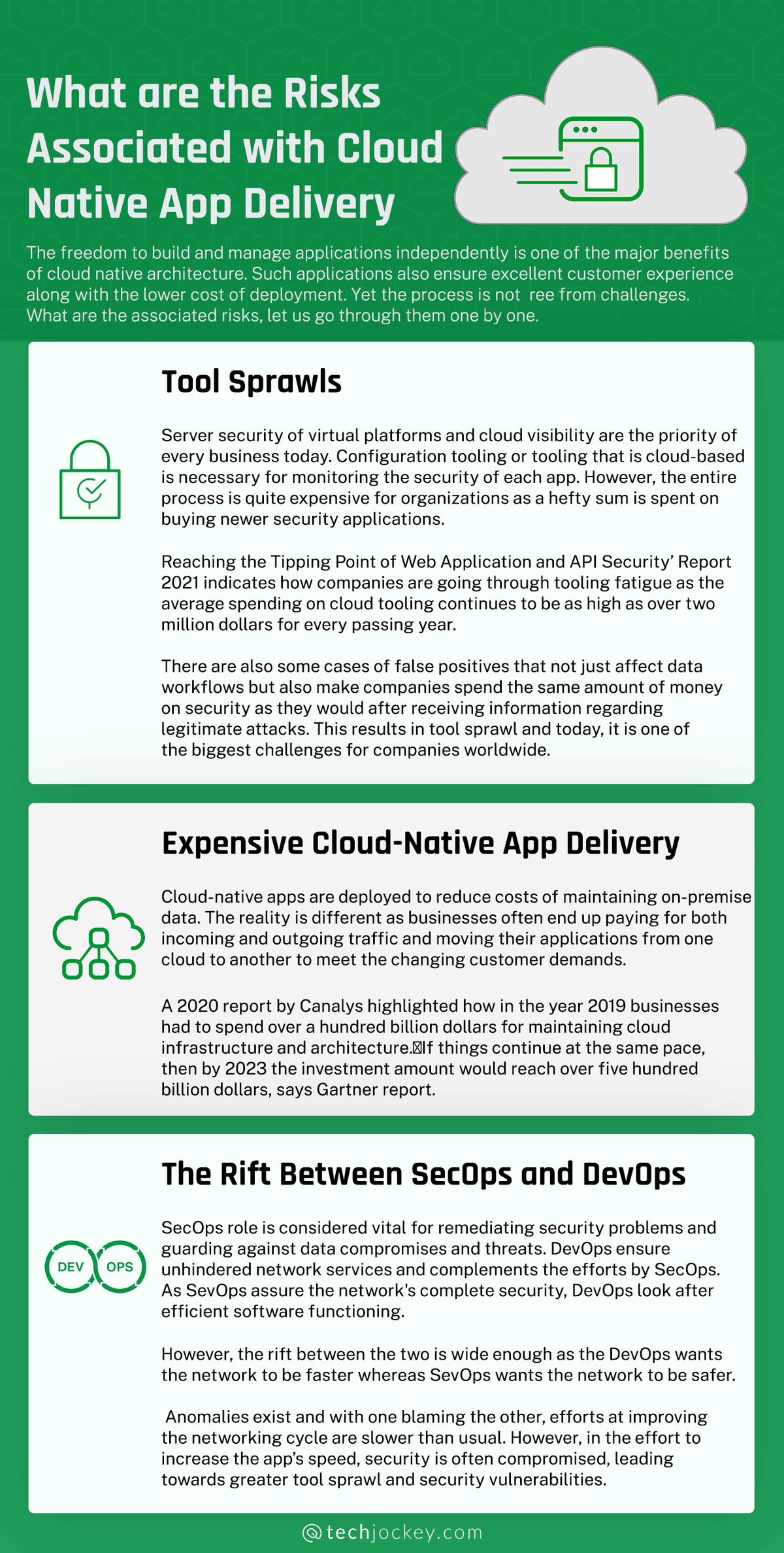
The freedom to build and manage applications independently is one of the major benefits of cloud native architecture. Such applications also ensure excellent customer experience along with the lower cost of deployment. Yet, the process is not free from challenges. So what are the associated risks, let us go through them one by one.
- Tool Sprawls
Server security of virtual platforms and cloud visibility are the priority of every business today. Configuration tooling or tooling that is cloud-based is necessary for monitoring the security of each app. However, organizations’ entire process is quite expensive as a hefty sum is spent buying newer security applications.
‘Reaching the Tipping Point of Web Application and API Security’ Report 2021 indicates how companies are going through tooling fatigue as the average spending on cloud tooling continues to be as high as over two million dollars for every passing year.
Some false positives affect data workflows and make companies spend the same amount of money on security after receiving information regarding legitimate attacks. This results in tool sprawl, and today, it is one of the biggest challenges for companies worldwide.
- Expensive Cloud-Native App Delivery
Cloud-native apps are deployed to reduce the costs of maintaining on-premise data. The reality is different as businesses often pay for incoming and outgoing traffic and move their applications from one cloud to another to meet the changing customer demands.
A 2020 report by Canalys highlighted how 2019 businesses had to spend over a hundred billion dollars for maintaining cloud infrastructure and architecture. If things continue at the same pace, then by 2023, the investment amount would reach over five hundred billion dollars, says Gartner report.
- The Rift Between SecOps and DevOps
SecOps role is considered vital for remediating security problems and guarding against data compromises and threats. DevOps ensure unhindered network services and complement the efforts by SecOps. As SecOps assure the network’s complete security, DevOps look after efficient software functioning.
However, the rift between the two is wide enough as the DevOps wants the network to be faster, whereas SecOps wants the network to be safer.
Anomalies exist, and with one blaming the other, efforts at improving the networking cycle are slower than usual. However, to increase the app’s speed, security is often compromised, leading towards greater tool sprawl and security vulnerabilities.
Related Categories: Load Balancing Software | Server Solution | Network Monitoring Tools | Virtual Server
Security of Cloud Native Applications: How Does NGINX Fit In
NGINX is capable of eliminating all the risks that come pre-set within a cloud environment. Here is how NGINX makes the architecture of cloud native apps secure:
- Reduced tool sprawls
NGINX offers enterprise-based standard services for decreasing tool sprawls across multi-cloud hybrid environments.
- NGINX App Protect- NGINX App Protect with NGINX Plus offers a load balancer for handling API gateways and reverse proxies with WAF. Your app will get maximum security whether it operates standalone or on managed public cloud services.
- NGINX Ingress Controller- NGINX Ingress Controller helps in traffic management for both cloud-based and containerized environments. NGINX App Protect can be easily integrated with NGINX Ingress Controller, and there is no need for separate WAF protection.
- NGINX Controller- NGINX Controller manages NGINX instances for both on-premise and cloud environments. The beta-based controller app with a security add-on secures both APIs and apps.
- Decreased cost & complexities
NGINX helps simplify not just the stacks but also saves apps from slowing down. Let us see how.
- Low latency- NGINX App Protect with NGINX Plus outperforms the existing WAFs through its super-fast speed for maintaining workloads, data, and security.
- Private offers- You can get access to annual ten to twenty percent discounts at AWS Marketplace. These would soon be available on Google Cloud and Azure platforms.
- Bringing teams together
The ever-widening gulf between SecOps and DevOps gets nullified with NGINX cost-effective solutions for automating security. Here is how NGINX does it:
- CI/CD integration- Use APIs to integrate NGINX with DevOps workflows. Here DevOps can successfully manage security, DNS, and load balancers, whereas SecOps can look after business-critical apps and enterprise networking security.
- Self-service- DevOps and SecOps together can prevent outages by allowing developers to manage apps and cloud-native services for sharing infrastructure resources.
Power Your Cloud Infrastructure with NGINX
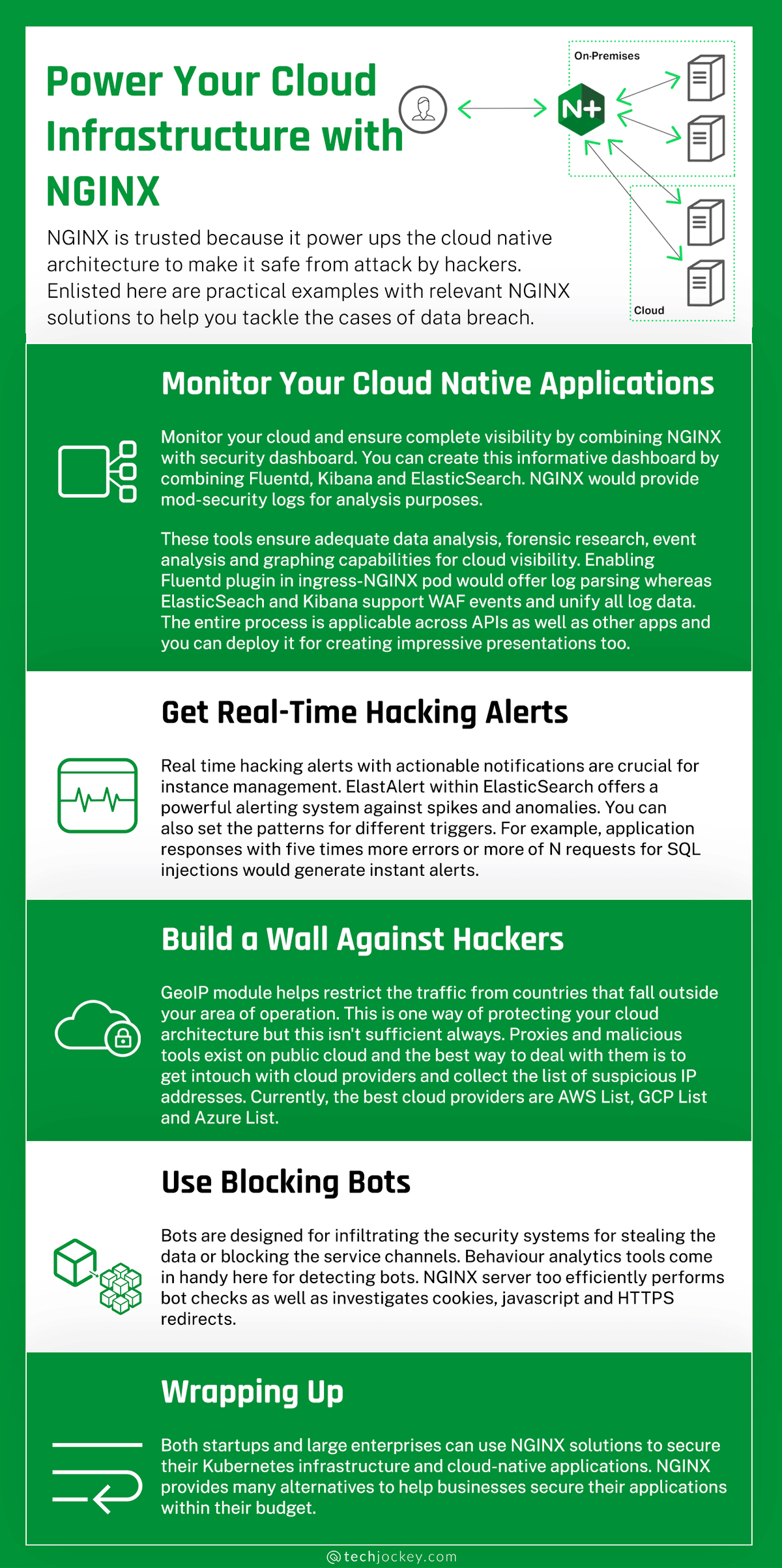
NGINX is trusted because it power-ups the cloud-native architecture to make it safe from attacks by hackers. Enlisted here are practical examples with relevant NGINX solutions to help you tackle the cases of a data breach.
- Monitor Your Cloud Native Applications
Monitor your cloud and ensure complete visibility by combining NGINX with a security dashboard. You can create this informative dashboard by combining Fluentd, Kibana, and ElasticSearch. In addition, NGINX would provide mod-security logs for analysis purposes.
These tools ensure adequate data analysis, forensic research, event analysis, and graphing capabilities for cloud visibility. For example, enabling Fluentd plugin in the ingress-NGINX pod would offer log parsing, whereas ElasticSeach and Kibana support WAF events and unify all log data.
The entire process is applicable across APIs and other apps, and you can deploy it for creating impressive presentations.
- Get Real-Time Hacking Alerts
Real-time hacking alerts with actionable notifications are crucial, for instance, management. ElastAlert within ElasticSearch offers a robust alerting system against spikes and anomalies.
You can also set the patterns for different triggers. For example, application responses with five times more errors or more N requests for SQL injections would generate instant alerts.
- Build a Wall Against Hackers
GeoIP module helps restrict the traffic from countries that fall outside your area of operation. This is one way of protecting your cloud architecture, but this isn’t always sufficient.
Proxies and malicious tools exist on the public cloud, and the best way to deal with them is to get in touch with cloud providers and collect the list of suspicious IP addresses. Currently, the best cloud providers are AWS List, GCP List, and Azure List.
- Use Blocking Bots
Bots are designed for infiltrating the security systems for stealing the data or blocking the service channels. Behavior analytics tools come in handy here for detecting bots. NGINX server too efficiently performs bot checks as well as investigates cookies, javascript, and HTTPS redirects.
Wrapping Up
Both startups and large enterprises can use NGINX solutions to secure their Kubernetes infrastructure and cloud-native applications. In addition, NGINX provides many alternatives to help businesses secure their applications within their budget.
Somya is one of the most experienced technical writers in the team who seems to be comfortable with all types of business technologies. She is a sensitive writer who ensures that businesses are able to find the right technologies through her writings. She would leave no stones unturned... Read more