How to Create Foolproof Disaster Recovery Plan with SonicWall

Cyberattacks are on the rise and affected organizations have to face long term repercussions based on the severity of the attack. Cyberattacks can disrupt business operations, damage IT infrastructure and resources, and cause huge monetary losses.
Cybercriminals often take advantage of existing vulnerabilities and find it easy to target small and mid-sized businesses. Small businesses have a higher risk of shutdown as they do not have the resources and budget to recover from such cyberattacks.
The Cost of Cybercrime Study by Accenture report highlights that while 43 per cent of cyber-attacks target small businesses, only 14 per cent are prepared to defend themselves.
SMBs need to have the right tools to protect their data and systems. In case of unexpected incidents, they must have the ability to recover the current data to new platforms or locations quickly.
SMBs (small and medium businesses) find it challenging to find an affordable yet effective backup and recovery solution within the constraints of their resources. In addition, it is hard for them to find a solution that is easy to implement and is affordable too.
SonicWall, a known name in the world of next-gen cybersecurity solutions and firewalls, offers cost-effective, end-to-end solutions to help SMBs create an effective disaster recovery and business continuity plan.
What is a Disaster Recovery Plan?
A disaster recovery (DR) plan is a formal document with detailed instructions on the actions to be taken to respond to unplanned events like cyber-attacks, natural disasters, equipment failure, and power outages, among other disruptions.
The IT disaster recovery response involves steps and tools to minimize the downtime of servers, employee workstations, and databases. The tasks include training employees with emergency procedures and creating another means of operation in advance for business continuity.
Preventing data loss is also essential for the smooth restoration of services. Disaster recovery avoids damage by backing up data in an alternate off-premises location that remains unaffected by the disaster.
This backup can recover systems and operations quickly after a disaster. Besides data recovery, a foolproof disaster recovery plan also includes network and access recovery.
Structure of Disaster Recovery (DR) Plan

A DR plan generally includes the following:
- Goals
A business needs to decide its goals to choose and implement a DR plan correctly. For this, you must calculate maximum downtime for every critical system, recovery time objective (RTO), maximum acceptable data loss, recovery point objective (RPO), etc.
Then, based on the outcome of these calculations, a business decides the frequency of data backup and other necessities during a disaster like personnel, facilities, budget, and so on.
- IT Assets/ Inventory
You must have a list of all the software and hardware assets owned, leased or used by your organization, along with their details. Based on the specifications, it becomes easier to categorize them and know which resources have the highest recovery priority during disaster events.
- Team
The organization must also specify people responsible for the execution of disaster recovery plan. This decision is important to train them beforehand and assign them different tasks in case of an event.
- Backup Processes
The DR plan must list backup procedures, detailing the location and process of backing up every data resource. You must also include the recovery procedure from backups.
- Disaster Recovery Sites
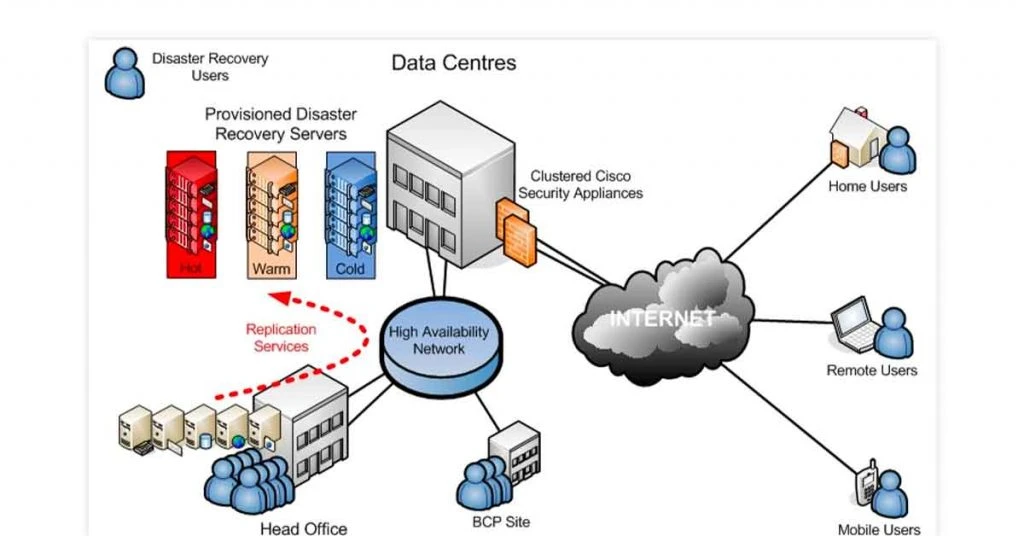
The disaster recovery plan must have an alternative data center with all critical systems in a remote location where data is backed up or replicated from the actual site. This hot disaster recovery site is used for all business operations in case of a disaster.
- Disaster Recovery Procedures
The DR plan must include your response to emergencies. The processes and steps must aim for instant last-minute backups, limiting damages, mitigating or eradicating cyber threats.
- Restoration
You should list complete procedures to recover from entire systems loss situations and resume all operations smoothly and quickly.
Data Security Practices to Ensure Business Continuity

Any disruptions in your business can break your business. You must be prepared for worst-case scenarios and follow the best data security practices to ensure that your work is not affected much in events of disasters.
Investing in fail-safe controls, cybersecurity, and other technology solutions can help you ensure smooth day-to-day operations. Some of the core data protection strategies for business continuity are:
- Follow Good Cybersecurity Practices
Cybersecurity awareness and relevant measures become highly important during disaster events. You require secure email controls and network security firewalls to prevent network breaches and attacks on partner or employee machines.
For example, you can use endpoint protection solutions like SonicWall Capture Client. It offers capabilities like vulnerability visibility, threat hunting, and malware protection.
Another example is the SonicWave Series access point or AP (outdoor mount/ ceiling mount/ wall mount) for wireless security. The APs can perform RF monitoring, wireless intrusion prevention/ detection, etc.
You can connect APs to SonicWall firewalls via SonicWall switches. It also offers other solutions for email security, cloud app security, and cloud edge secure access that SMBs can use.
These security practices help ensure that networks, data, and users are protected in times of disaster due to targeted attacks like ransomware and phishing. In addition, good practices can prevent malicious files from executing even if a machine is infected.
- Network and Data Access
The disaster recovery plan needs to be accessible after a disaster. If connectivity is down to the main site, but you can’t reach the secondary site either, then having an alternative option becomes useless.
You must have access to the network, email, etc. You can do this by storing data and email repositories in the cloud instead of an on-prem server. Cloud storage will ensure continuous communication even when connectivity is down.
You can also use solutions like SonicWall Secure Mobile Access (SMA) appliance for automatically setting up a VPN to the nearest online site and rerouting access whenever required.
- Have Multiple Communication Options
In times of disaster, your employees need to communicate with customers, partners, and vendors to take appropriate actions. However, email, which serves as the main form of professional communication, may not be available.
So, it becomes crucial to have backup options like WhatsApp, Slack, Microsoft Teams, and social media platforms like Twitter. These options make it possible for internal teams to coordinate for recovery and manage public communications.
- Have a DR and Business Continuity Plan
After a disaster, it is hard for teams to make accurate decisions under pressure. A well-prepared disaster recovery and business continuity plan ensures that you have all the instructions and procedures.
Also, training and simulations beforehand help ensure that all departments like HR, IT, and communications can successfully implement the plan.
Steps to Create an Effective IT Disaster Recovery Plan
Creating a DR plan requires in-depth research into the requirements and risks for your organization. It also needs careful planning, taking into consideration the suggestions of all stakeholders. Steps to create a foolproof DR plan are:
- Mapping Out Assets
Knowing what software, network equipment, hardware, cloud services you have is important to plan how to protect them. Every asset must have details like vendor and version, physical or virtual location, networking parameters, how they connect with other assets, etc. These details are necessary to classify critical data in these assets too.
- Classifying Assets
Once you know the importance of individual assets and how they are used, you can classify them as high, medium, or low impact assets. High impact assets would mean that they have the potential to disrupt business operations significantly and are hence critical.
- Identifying Threats
Doing risk assessment for individual assets and the entire business is essential to know the probable causes of service interruption. You can get insights from the department staff members and identify the threats for critical systems.
There are analytics solutions from vendors like SonicWALL that you can also use to gain knowledge of your network.
- List Down Recovery Objectives
You must know the outcome of potential threats and interruptions to critical systems. Consult the staff and senior management to know the impact per minute, hour, day, and so on. Based on this information, you can define the Recovery Pont Objective (RPO) and Recovery Time Objective (RTO).
RPO only focuses on data to know the ideal backup frequency. In contrast, RTO focuses on the downtime of assets and processes to decide relevant resource allocation in the time of disaster for business continuity.
- Choose Recovery Setup and Tools
You need to decide your course of action during a disaster based on your information. Some choices include deciding the location of the hot DR site, required backups or replicas, cloud-hosting vs self-hosting, partners to help with the setup, etc.
- Budget
The management must invest in the right DR technology based on the identified risks and the support that different options can provide. Then, based on your RPO/RTO and other needs, you must choose the most optimal solution.
- Approval and Circulation
The final draft needs to be approved by the management after changes have been made according to their feedback in the previous stages. Once you have a consensus, the final plan is signed off.
Finally, the DR procedures document is circulated to the senior management and others involved, such as the DR team.
- Test and Review
You must conduct feasible disaster drills from time to time to test the plan. Such drills help you check if the staff acts as per the plan. It also enables the modification of procedures and plans that are not effective enough.
Periodic reviews help ensure that the plan is relevant based on the current IT setup and organizational structure.
Top SonicWall Solutions for Effective Disaster Recovery Plan
You can use the following tools for setting up your data recovery infrastructure:
- Data Recovery
SonicWall next-generation firewalls protect devices against data loss from cyber-threats. You can choose from entry-level TZ series, mid-range NSa series, and high-end NSsp series.
SonicWall Continuous Data Protection (CDP) offers a foolproof, disk-based backup and recovery solution for SMBs. It ensures reliability and high performance with RAID 5, GbE connectivity, etc.
In addition, it uses industry-standard encryption and can instantly recover data onto new devices. You also get regular email alerts for all activities.
It automates tedious tasks and ensures that there is no burden on IT staff to protect SQL, Exchange, and other applications.
In addition, the end-to-end solution provides site-to-site/ offsite data backup, local archiving and other flexible options to safeguard data. It also ensures that multiple historic versions of all files are available.
- Network Recovery
Network disasters can occur due to failure in services or hardware. SonicWall offers cost-effective, easy to deploy network security appliances to deliver wireless LAN (WLAN) connectivity and other security features.
In addition, SonicWall Secure Distributed Wireless Solution distributes SonicPoint 802.11a/b/g wireless APs throughout site location, which these appliances can automatically configure.
When the broadband connection fails, network appliances automatically move to alternate WAN and provide continuous uptime till the fixed connection gets re-established.
- Access Recovery
With the growth of remote work culture, having secure remote access (SRA) and secure mobile access (SMA) solutions as part of disaster recovery has become essential.
Both options aim to provide a clientless access method to network resources and apps, which is highly useful for mobile and remote employees.
SonicWall SRA solutions like Aventail E-Class SRA SSL VPN provide network managers with easy access control. It helps managers provide authorized access to clients and other stakeholders from various cross platform devices.
As a secure access gateway, it enables remote access to intranets, servers, applications, files, and other wireless or wired network resources via a web browser. This option is also useful for technicians in providing remote support to users.
Conclusion
Disaster recovery preparedness is crucial for all organizations, from large enterprises to SMBs. Products from vendors like SonicWall can help you reduce upfront to purchase, preparedness and recovery costs while improving ROI.
Related Categories: Network Security Solution | Mobile Device Management (MDM) Software | Data Security Software | Mobile Security Software
Ayushee is currently pursuing MBA Business Analytics from SCMHRD, Pune with a strong background in Electronics and Communication Engineering from IGDTUW. She has 2 plus years of full-time work experience as an SEO content writer and a Technology Journalist with a keen interest the amalgamation of business and... Read more