Summary: Malware, social engineering, and ransomware attacks are some of the most common cyber threats that can lead to data theft and financial loss. In this article, we will learn more about these cyberattacks in detail.
With the growing reliability on technology, individuals, businesses, and governments face a growing array of cyber threats. From malicious software updates to hacking techniques, the landscape of cybersecurity threats is ever changing and needs constant vigilance to prevent data breaches. In this article, we will go through multiple types of cybersecurity vulnerabilities to help you prevent cyber-attacks within your organization.
What are Cybersecurity Threats?
Cybersecurity threats are a kind of acts performed by people with harmful intent to steal sensitive data or cause disruption to computer systems. Some common categories of cyber threats include malware, social engineering, denial of service (DoS), injection attacks, man in the middle (MitM) attacks, etc. In this article, you will learn about each of these categories.
Common Sources of Cyber Threats
Cyber security threats can come from multiple sources. Here are some of the most common sources of cyber threats.
- Nation States: Many hostile countries launch cyber-attacks against many local companies and institutions to interfere with communications. This will cause disorder and damage in the country.
- Terrorist Organizations: They conduct cyber-attacks to destroy the country’s important infrastructure, disrupt economies, threaten national security, and harm the citizens.
- Criminal groups: Many criminal groups aim to crush computing systems for monetary benefits. They use spam, phishing, spyware, etc., for extortion and theft of sensitive information.
- Hackers: Hackers target specific organizations through various techniques including malware and spyware. They do this because of personal gain, financial gain, revenge, etc.
- Malicious Insiders: Malicious insiders are majorly employees of the organizations who abuse their positions to steal data or damage systems for monetary or personal gain.
Types of Cybersecurity Threats
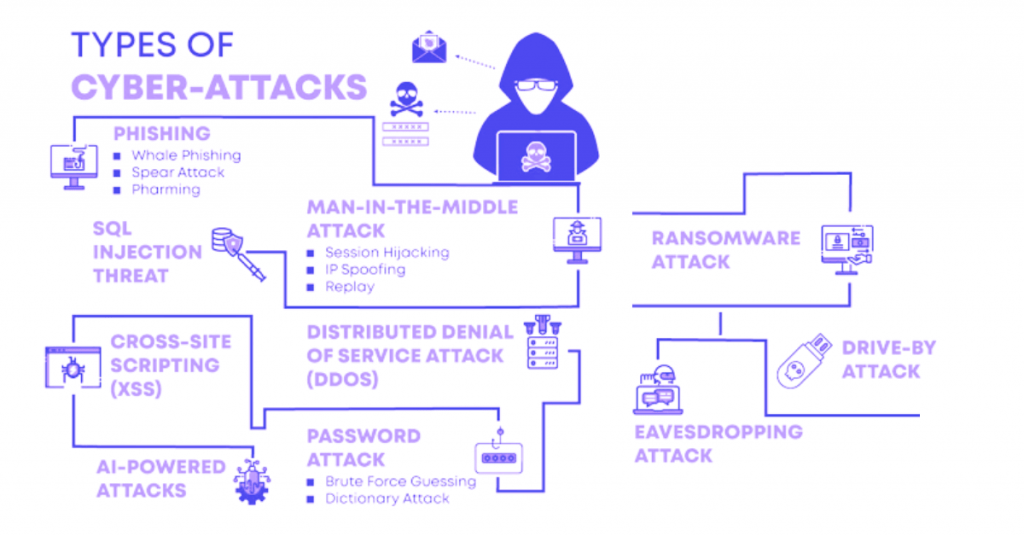
Malware Attacks
Malware attacks are the most common types of cyber threats that happen when you click on a link received from an untrusted site and email. When this attack happens, it can collect sensitive data, blocks network access, shut down systems, etc.
Example: Viruses, Worms, Trojans, Ransomware, Cryptojacking, Spyware, etc.
Social Engineering Attacks
Social engineering attacks are accomplished by tricking people to provide sensitive information or unwillingly installing malware on their systems. The attacker manipulates the victim in a way that he or she performs actions that may lead to security breaches.
Examples of Social Engineering Attacks: Baiting, Pretexting, Vishing, Smishing, Piggybacking, Tailgating, etc.
Supply Chain Attacks
Supply chain attacks are a kind of cyber-attack which targets the weaker links of an organization’s supply chain. This supply chain is the chain of all people, resources, technologies, and activities involved in the production and sale of a product. By attacking the supply chains, the hackers try to exploit the relationship between the organization and parties involved for their own monetary benefits.
Examples of Supply chain attacks: Compromise development pipelines, Compromise of code signing procedures, automated updates to hardware,
malicious code pre-installed on hardware, etc.
Man-in-the-Middle Attack
In this type of attack, the attacker intercepts the communications between the two endpoints. The hacker eavesdrops on the communication to steal the sensitive information and even impersonates the parties involved in the communication for stealing information.
Examples of Man-in-the-Middle Attack: Wi-Fi eavesdropping, Email hijacking, DNS spoofing, IP spoofing, HTTPS spoofing, etc.
Denial-of-Service Attack
A Denial-of-Service (DoS) attack is a kind of attack that shuts down a system and network that makes it inaccessible to the users. These attacks accomplish it by flooding the system or network with traffic to crash it that prevents the legitimate users from using the required services.
Examples of Denial-of-Service Attack: HTTP flood DDoS, SYN flood DDoS, UDP flood DDoS, ICMP flood, Network Time Protocol (NTP) amplification, etc.
Injection Attacks
Under the injection attack, the hacker inserts malicious inputs into an application’s source code. The inserted input is then processed by the server as part of query or a command that alters the application working. Once the attack is accomplished, the hacker can easily get access to the sensitive data and even comprise the entire system.
Examples of Injection Attacks: SQL injection, Code injection, OS command injection, lightweight Directory Access Protocol (LDAP) injection, XML eXternal Entities (XXE) Injection, execute server-side request forgery (SSRF), Cross-Site Scripting (XSS), etc.
Why is it Necessary to Get Protection against Cyber Threats?
The protection against cyber threats is important to safeguard and protect sensitive data, personal information, or any other confidential information. Here are some other reasons why you need to get protection against cybersecurity threats:
- Maintaining brand’s reputation
- Reducing third party security breaches
- Protecting personally identifiable information (PII) of your customers
- Maintaining regulatory and legal compliance
- Maintaining credibility and trust among customers
- Reducing the financial loss resulting from data breaches.
Learn More: Cybersecurity Tips & Best Practices in 2023
Types of Cybersecurity Solutions to Curb Cyber Attacks
Cybersecurity solutions are a type of tool and services that can help in mitigating the effects of cyber-attacks. These solutions come with specific features to deal with a particular type of cyber threats. Here are some of the most common types of cybersecurity solutions:
- Application Security Solutions: For identifying vulnerabilities in an app during and after development.
- Endpoint Security Solutions: These solutions are deployed on endpoint devices such as servers to prevent malware and unauthorized access.
- Network Security Solutions: These are used for monitoring network traffic, identifying malicious traffic, and mitigating network threats.
- Internet of Things (IoT) Security Solutions: These types of solutions help in gaining visibility and controlling the IoT devices’ network.
- Cloud Security Solutions: these are used to gain visibility and control over public, private, and hybrid cloud environments. Further, they also help in identifying vulnerabilities and remediating them.
Cybersecurity Threats and Trends for 2023
As the new vulnerabilities and attack vectors are emerging, there are a lot of new cyber threats that have come to the forefront in addition to the existing ones. Here are some of the emerging cyber threats that have affected businesses in 2023.
- Use of Artificial intelligence by hackers to hack systems
- Hacking vehicle and IOT devices to steal data through software
- Misconfiguring cloud environments to steal information
- Undertaking state-sponsored attacks due to geolocation situations
- Using Malvertising to inject malicious code into digital ads
Conclusion
In today’s digital landscape, it is imperative for individuals and organizations to stay informed about emerging cyber threats and implement effective security measures. Being aware of the types of cyber threats, you will be able to mitigate the effects of these threats and keep all the data protected against breaches in both the present and future.
FAQs
What is a threat in cybersecurity?
A threat in cybersecurity is a kind of act performed by a person to steal sensitive information or damage the computer systems for his own monetary benefits.
What are the six pillars of cybersecurity?
The six pillars of cybersecurity include governance, compliance, risk management, education, incident management, and technical controls.
What are the cyber threats in 2023?
Phishing, social engineering, data theft, ransomware, and software supply chain attacks are the most common types of cyber threats in 2023.
What are the types of cyber security?
There are different types of cyber security including Application security, Cloud security, Endpoint security, Mobile security, Network security, Endpoint security, etc.
How does cyber security work?
Cybersecurity works through implementation of preventive measures like firewalls and software updates to block malicious activities.
What are top 10 cyber security threats?
The top 10 cyber security threats are Phishing, Ransomware, malware, social engineering, Man-in-the-middle attack, Trojans, Denial-of-service attack, SQL injection, Cryptojacking.
Varsha is an experienced content writer at Techjockey. She has been writing since 2021 and has covered several industries in her writing like fashion, technology, automobile, interior design, etc. Over the span of 1 year, she has written 100+ blogs focusing on security, finance, accounts, inventory, human resources,... Read more








.png?d=100x100)